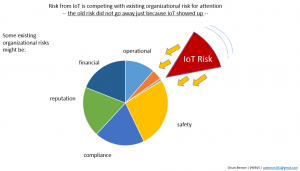
To achieve IoT Systems ROI and to ensure non-degradation of an institution’s existing cyber-risk profile, IoT Systems must be manageable. In turn, in order to build IoT Systems manageability, institutions will need to manage their IoT Systems risk with non- traditional approaches that includes assigning IoT endpoints (the ‘things’ in IoT) to risk categories that can be independent of the underlying technologies and vendors.
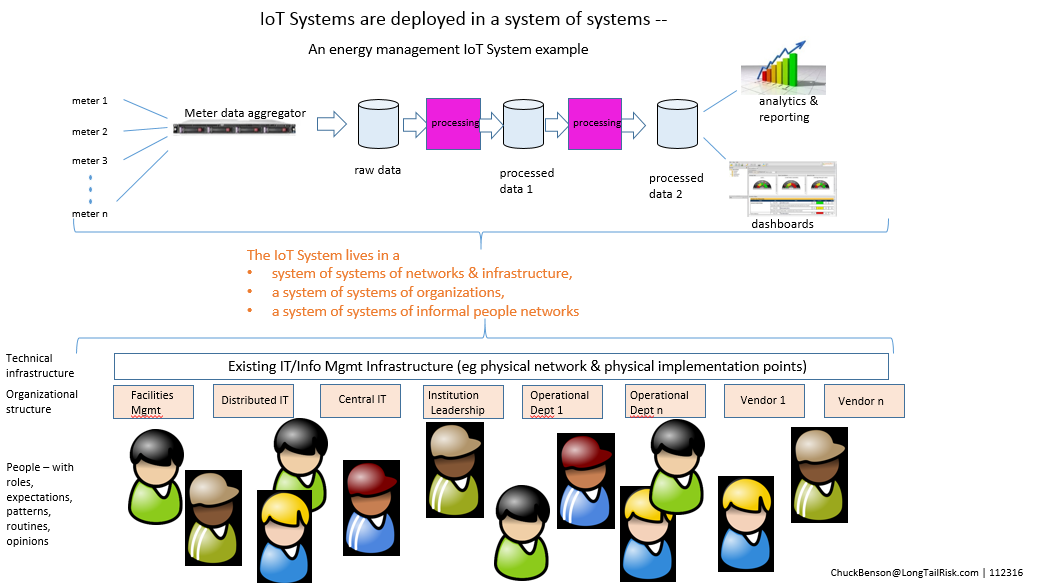
IoT Systems are increasingly complex to implement, manage, and to establish system ownership in institutions, whether cities, Higher Education institutions, or corporate campuses. In turn, an institution’s IoT Systems Portfolio – a systems of systems – rapidly deepens the complexity. We will need to tackle the problems and challenges in new ways and with new organizational concepts if we are to have an opportunity for well-managed and reasonably risk-mitigated systems. This includes thoughtful inter-organizational planning, partnerships, and development of a more common language between central IT, distributed operational organizations and departments, and vendors. Further, this will be required to establish system ownership and management plans between organizations such as facilities organizations, central IT, research groups, vendors, and others. One step toward this objective is identifying things to be managed independently of the technologies and vendors implementing them — a Risk-Managed Set of Networked Things.
Central IT won’t own all of the IoT Systems
Traditional enterprise network and system management tools, staffing models, and even language are ill-equipped to address this rapidly changing technology. Historically, network and system management tools have all been within the purview of central IT. Central IT will not be able to keep up with the accelerating growth of IoT Systems across an institution. Just like central IT organizations cannot manage every user/academic/business application on their networks (or even many of them), central IT will not be able to support all of the IoT Systems either. Business owners — operational (academic in the Higher Ed case) and administrative — will have to share that load. That’s better for them too — they are closer to the problem and have a truer understanding of desired outcomes from the system. Implementing this coordination across two or more organizations in the institution is new work though. There are not great precedents for this. Institutions, particularly Higher Education institutions, are known for their bureaucracies within bureaucracies, entrenched ways, and “cylinders of excellence..” (aka silos) .
In a similar fashion facilities management organizations have substantial skill sets in building in and integrating equipment into built environments whether they are buildings or spaces. However, facilities management organizations don’t have network design, implementation, network management, and traditional server management skill sets. Finally, while operational departments, whether acting independently or in collective partnerships with other operational departments, know what they want systems to do and comment on performance, they do not have the required skill sets that facilities management and central IT groups bring to the table.
This organizational-spanning nature of IoT Systems in institutions make establishing ownership and a post-implementation management plan particularly challenging.
Designing for & building IoT System manageability
The growth in institutional system count, system complexity, and system interdependency makes for rapidly evolving systems management and owner environments for Higher Ed institutions. We have to take definitive steps to make things more manageable. That is, we have to design for system manageability. Applying historical and traditional tools and organizational approaches to this rapidly changing environment will no longer be sufficient.
A core component of any framework to facilitate manageability is a language, or at least shared concepts, that support it. In turn, a substantial objective of that shared language development (shared, for example, between central IT, facilities, and operational users) is to develop structures that make the systems more manageable. This sounds obvious, but in our complex environments and with our dwindling availability of time and cognitive bandwidth, it is easy to lose sight of this objective.
Agreeing on what is being managed
Before different organizations within an institution can establish those manageability- facilitating-structures and figure out how to partner, establish ownership, and mitigate risk to institutional systems, they have to be able to mutually identify and agree upon what is being managed. What is the set of things — devices, systems, spaces, buildings, infrastructure, etc — that we care about managing, from both operational and risk mitigation standpoints?
In days of relatively simpler systems, sets of networked things/devices to be managed were often defined by the network itself and/or systems on the network and/or the particular brand of technology supporting the network. Further, these networked things/devices were typically run by central IT organizations and these organizations were comfortable with using locally understood network terminology and concepts to define that set of things. Examples include — devices/things on a particular subnet or set of subnets, devices/things behind a particular firewall, on a particular VLAN or VRF, etc.
These examples above don’t mean much to potential system owners that are business organizations and/or academic organizations. The terms used are way too abstract, jargon-y, and/or colloquial. The cross-organizational planning and coordination needed for IoT Systems implementations and subsequent management cannot occur if participating groups can’t mutually identify what is to be managed.
Also problematic in trying to apply these old approaches of identifying things and systems to be owned, operationally managed, and risk-managed is that it is easy to slip into the high-granularity/high-entropy of technical details when the initial conversation is simply identifying and agreeing upon what is to be managed. Because these new and rapidly evolving technologies are increasingly complex, requiring increasingly deep technical skill sets, conversations in technical detail can be challenging even for technical professionals and effectively useless for potential academic and business partners and systems owners.
Finally, sets of things/devices to be managed might involve multiple technologies — eg maybe partially wired, partially wireless/near-field, on a VRF, behind a firewall, etc. So using a technology as a defining mechanism is further unhelpful. While a particular technology or network might happen to align well with a business need for defining a group of assets to be managed, we don’t want to start with that assumption.
IoT System Manageability Groups – A Risk-Managed Set of Networked Things
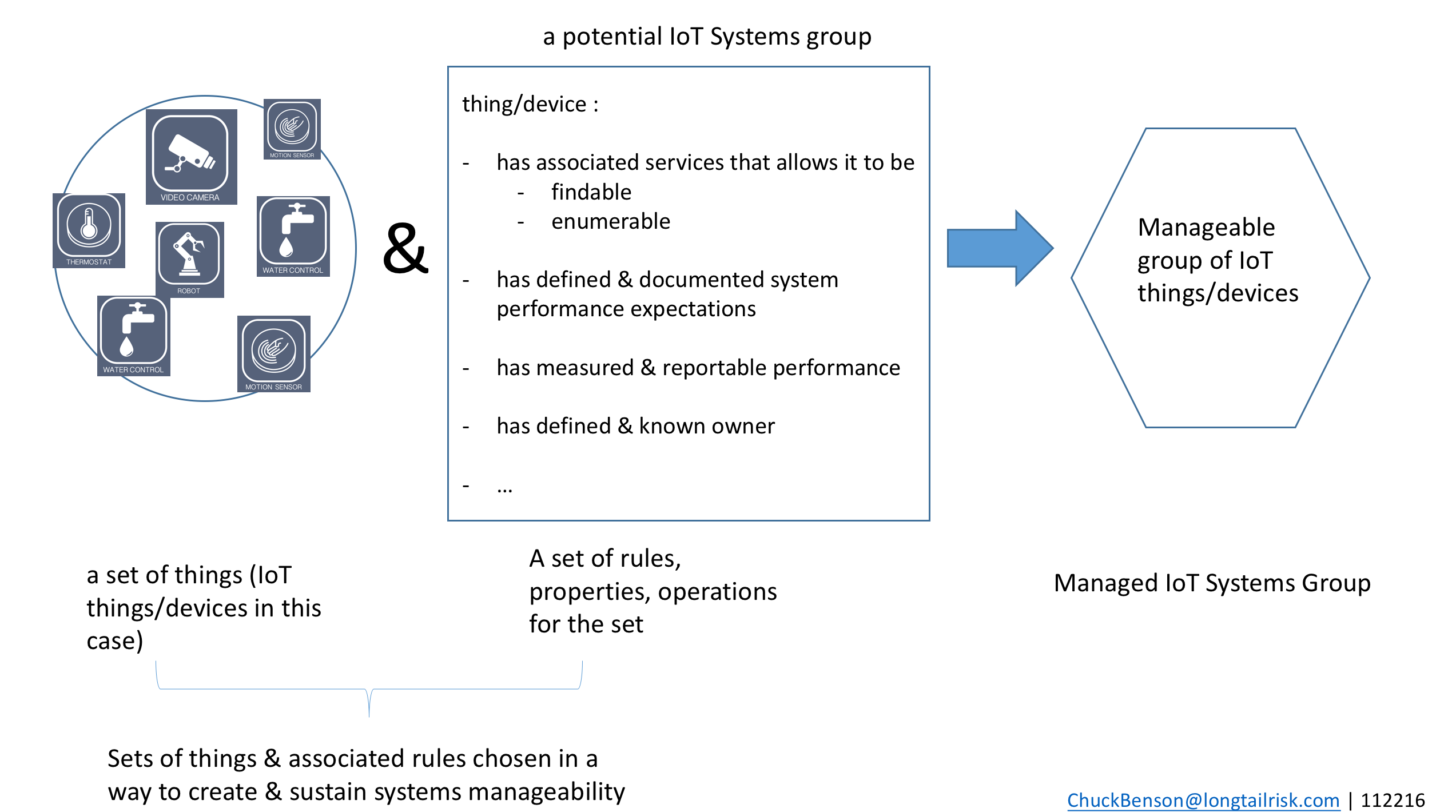
To address these shortcomings, we can consider a Risk-Managed Set of Networked Things (RMSONT). In this approach, we work to establish sets of networked things based on what best enhances manageability of the system. This is independent of underlying implementing technologies, particular vendors, and existing organizational charts.
What constitutes IoT System manageability?
A managed IoT System will have at least these attributes:
- the IoT System was selected methodically and with purpose
- the IoT System is named & known
- the system has a common name that is known, shared, & published to participating parties (eg central IT, facilities management, operational departments, etc)
- devices/things of the IoT System are enumerable
- that is, via network process the device can be known and named
- IoT System owners identified
- IoT System component owners identified
- satisfactory system performance is defined
- system performance is measured
- system performance is reviewed by business owners and systems support providers
- estimates of total costs are established and shared — includes IT and Operational Technology (OT) costs
- other
What are the qualities/attributes of a thing/device?
Things/devices in IoT Systems have at least these qualities or attributes —
- a location
- a function (what is it supposed to do)
- an IP address; a MAC address
- a power requirement
- an associated data aggregator or controller
- supports a user, users, or population (department, organization, constituency, etc)
- rate of failure (estimated or known)
- other
Creating a Risk-Managed Set of Networked Things
The #1 goal is to build and enhance IoT Systems manageability. A risk-managed set of networked things is established to create a manageable group. This could be a group managed by the business consumer or an institutional service organization such as facilities management or central IT — whatever best facilitates system ownership and management.
Multiple sets of risk-managed things can be created to facilitate overall system manageability. One example of a set of risk-managed sets might be:
- law enforcement/security office owns and manages a set of networked video cameras (possibly with support from central IT, facilities management, local IT, vendor, etc)
- in an academic setting, a researcher that uses a specialized HVAC IoT System with sensors, actuators, and data aggregation to provide tight environmental control of their research environment might be a logical choice to own that system
- a metering system might best be managed by the institution’s energy management office
- a building manager might have a risk-managed set of networked things local to their particular building, but of different types of things— surveillance cameras, energy management system, etc
In general, getting those most familiar with the IoT System’s performance expectations and actual performance into a system management role is probably a good idea.
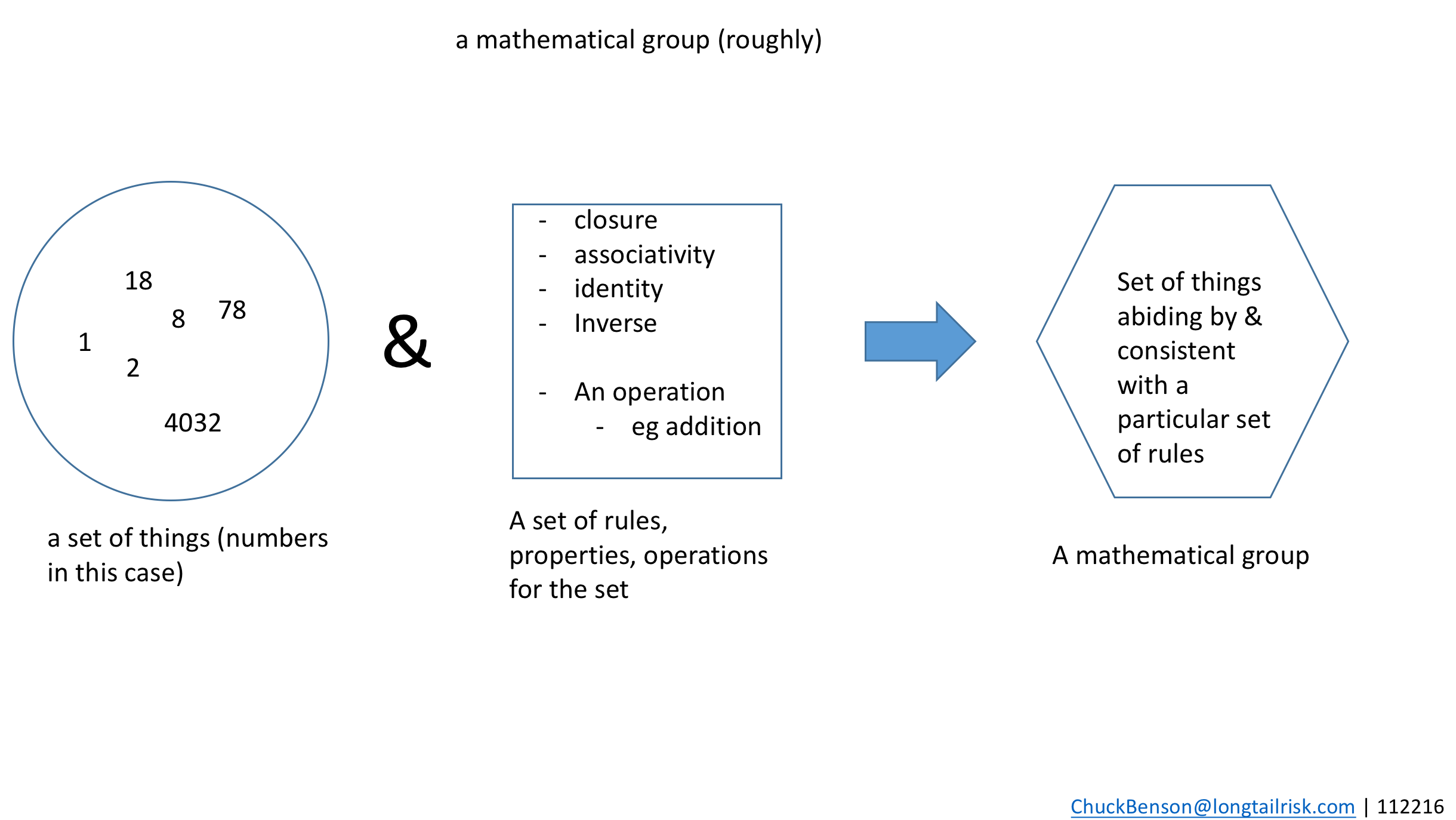
As we talk about sets of things, and particular kinds of sets of things, we can borrow lightly from the mathematical idea of groups.
As I understand it, mathematical groups are:
- Sets of things
- These things abide by or participate in some set of rules
Similarly, a Risk-Managed Set of Networked Things, can be:
1. A set of networked and computing things/devices (that interact with the environment)
2. These things/devices participate in or are governed by some sort of network management processes and human management processes — eg automated network device enumeration/inventory, device health/responsiveness, etc
To borrow from Offspring’s social commentary (and popular song) on gang membership, colors, and violence in Come Out and Play, the theme of IoT Systems and network segmentation seems to be, “you gotta keep ‘em separated.” The problem is that that is not as easy as it seems.
Network segmentation has been all the rage as an answer to IoT Security and risk mitigation. However, as we’ve seen, network segmentation alone is not sufficient. Risk-managed sets of things need to be thoughtfully chosen, the rules and operations supporting that set of things needs to be thorough, and systems owners thoughtfully coupled with systems in order to achieve manageability.
We can manage IoT Systems within our institutions. And we can manage portfolios of IoT Systems within our institutions. However, we need to acknowledge that these are different kinds of systems and that our existing traditional IT systems operational and risk management approaches are likely insufficient. From that point we can sculpt and evolve new management approaches that facilitate successful, well-managed IoT Systems portfolios.