Tag Archives: iot
More ghosts in the machine
It turns out that the microprocessors that are on almost every SD memory device produced are accessible and fully programmable. This has significant implications for security and data assurance and is an archetypal example of what we are facing regarding new risks from the Internet of Things (IoT).
Two researchers, Sean Cross who goes by xobs and Andrew Huang, aka bunnie, presented at Chaos Communication Congress last week and simultaneously released a blog post on their discovery and approach.
SD devices are ubiquitous and found in smart phones, digital cameras, GPS devices, routers and a rapidly growing number of new devices. Some of these are soldered onto circuit boards and others, probably more familiar to us, are in removable memory devices developed by Kingston, SanDisk and a plethora of others.
Microprocessors built into memory devices?
According to the presentation and Bunnie’s blog post, the quality of memory in some of these chips varies greatly. There is variance within a single manufacturer, even a highly reputable one like SanDisk. There is also variance because there are many, many SD device manufacturers and a lot of those don’t have the quality control or reputation of the larger companies. In his presentation, he gives a funny anecdote involving a fabrication factory tour of a manufacturer in China that was complete with chickens running across the floor.
So, on any memory device produced, there are bad sections. Some devices have a lot more than others, eg up to 80% of the memory real estate is unusable. That’s where the onboard microprocessors come in. These microprocessors run algorithms that identify bad memory blocks and perform complex error correction. Those processes sit between the actual physical memory and the data that is presented at the output of the card. On a good day, that data that the user sees via the application on the smart phone, camera or whatever is an error-corrected representation of what the actual ones and zeros are on the chip. Ideally, that data that ultimately reaches you as the user appears to be what you think your data should be.
“Mother nature’s propensity for entropy”
Huang explains that as business pressures demand smaller and smaller memory boards, the level of uncertainty of the data in the memory portion of the chip increases. This in turn increases the demand on error correction processes and the processor running them. He suggests that it is probably cheaper to make the chips in bulk (with wide quality variance) and put an error-correcting processor on the chip than it is to produce a chip and then fully test and profile it. In their research, it was not uncommon to find a chip labelled with significantly smaller capacity than that available on the actual chip.
What Cross and Huang were able to do is actually access that microprocessor and run their own code with it. They did this by development of their own hardware hacking platform (Novena), physically cracking open a lot of devices (breaking plastic), lots of trial and error, and research on Internet search sites, particularly Google and China’s Baidu.
The fact that there is a way to get to the processes that manipulate the data sitting on the physical memory has significant implications. Ostensibly, these processors are there to support error correction so that your data appears to be what you want it to be. However, if (when) those processors are accessed by a bad guy:
- the bad guy can read your data while it’s on its way to you, ie Man In the Middle (MITM) attack
- the bad guy can modify your data in place — to include modifying encryption keys to make them less secure
- the bad guy can modify your data while it’s on its way to you
- others
Illusion of perfect data
At about 7:28 in the video, Huang makes a statement that I believe captures much of the essence of the risk associated with IoT:
“… throw the algorithm in the controller and present the illusion of perfect data to the user …”
While this specific example of IoT vulnerability is eye-opening and scary, to me it is a way of showcasing a much bigger issue. Namely, the data/information presented to us as a user is not the same data/information that is stored somewhere else. That physically stored data has gone through many processes by the time it reaches the user in whatever software/hardware application that they are using. Those intermediate processes where the data is being manipulated, ostensibly for error correction, are opportunities for misdirection and attack. Even when the processes are well-intentioned, we really don’t have a way of knowing what they are trying to do or if they are being successful at what they are trying to do.
What to do
So what can we do? Much like watching a news story on TV or reading it online, the data/information that we see and use has been highly manipulated — shortened, lengthened, cropped, edited, optimized, metadata’d, and on and on — from its original source.
Can we know all of the processes in all of the devices? Unlikely. Not to get too Matrix-y, but how can we know what is real? I’m not sure that we can. I think we can look at certifications of some components and products regarding these intermediate processes, similar to what Department of Defense and other government agencies wrestle with regarding supply chain issues. However, there will be a cost that the consumer feels for that and the competition driven from the lower cost of non-certified products will be high. Maybe it’s in the public interest that products with certified components are publicly (government) subsidized in some way?
An unpleasant pill to swallow is that some, probably substantial, portion of the solution is to accept that we simply don’t know. And knowing this, modify our behavior — choose what information we save, what we write down, what we communicate. It’s not the idyllic privacy and personal freedom place that we’d prefer, but I think at the end of the day, we won’t be able to get away from it.
slides from conference
Bunnie blog
Xobs blog
[MicroSD image from Bunnie blog]
We’re gonna need a bigger boat — FTC ruling on (at least one) IoT device
 I missed this when it came out in last fall, but it is a step in the right direction. An IoT manufacturer has settled with the FTC for “failure to reasonably secure IP cameras against unauthorized access” for their cloud-connected IoT video camera. According to the complaint, the FTC went after the manufacturer, TrendView, for several issues with its SecurView cameras to include:
I missed this when it came out in last fall, but it is a step in the right direction. An IoT manufacturer has settled with the FTC for “failure to reasonably secure IP cameras against unauthorized access” for their cloud-connected IoT video camera. According to the complaint, the FTC went after the manufacturer, TrendView, for several issues with its SecurView cameras to include:
- transmitted user login credentials in the clear
- user credentials stored in the clear
- vendor failed to implement a process to actively monitor security vulnerability reports from third-party researchers
- lack of security architecture review
- lack of security review and testing during software development
The FTC alleged that these, among others, contributed to putting users at “significant risk.”
Also, according to this article at ReadWrite.com, a security researcher figured out that one of the Internet domain names that the manufacturer had listed as a secure host for video streams was not registered! The researcher, Craig Heffner, now with Tactical Network Solutions, was able to acquire that domain name. If desired, he could have then picked up all of the video streams from users pointing their devices to that domain. Since the users were advised by the manufacturer to use that domain name, the users would have no idea that their data could have been streaming to someone else.
And the networked-based video surveillance business is booming. Per the FTC complaint, IP (Internet Protocol) video camera sales were $6.3 million in 2010, $5.8 million in 2011, and $7.4 million in 2012. Remember, this is just one company’s products. There are many others and the number of manufacturers will continue to grow.
Without such challenges by an agency like the FTC, there is little to motivate manufacturers to supply products that have been developed with reasonable security oversight in the process. That said, with tens of billions of IoT devices expected in the next few years, I don’t think that the FTC, as it stands, is going to be able to make a huge dent. It seems to me that an entirely new way of viewing and enforcing privacy law is required and I don’t see that coming in the near future.
As Brody observed in the movie Jaws in 1975, “We’re gonna need a bigger boat.”
Channeling the ghost in the machine
 A team of researchers has identified a way to extract full 4096-bit RSA decryption keys just by listening to (detecting) the sounds generated by a computer. Sound patterns can be associated with particular processes occurring on the computer. Of special interest are the unique sound patterns generated when cyphertext (text that has been encrypted) is in the process of being decrypted. The researchers claim that in less than an hour a decryption key can be identified by analyzing sound patterns generated by decryption of particular cyphertexts. Interestingly, this is not sound generated by fans, hard drives, or speakers, but rather sound generated by electronic components such as inductors and capacitors.
A team of researchers has identified a way to extract full 4096-bit RSA decryption keys just by listening to (detecting) the sounds generated by a computer. Sound patterns can be associated with particular processes occurring on the computer. Of special interest are the unique sound patterns generated when cyphertext (text that has been encrypted) is in the process of being decrypted. The researchers claim that in less than an hour a decryption key can be identified by analyzing sound patterns generated by decryption of particular cyphertexts. Interestingly, this is not sound generated by fans, hard drives, or speakers, but rather sound generated by electronic components such as inductors and capacitors.
Handling interference
Most of the information-yielding acoustics occur above the 10 KHz range. Fan noise and typical room noise generally occurs at lower frequencies and can be filtered out.
Depending on the environment, some keys can be decrypted by using a smart phone within approximately 30 cm. Ranges of up to 4 meters have been successful using specialized equipment such as parabolic microphones.
Different computers have different signatures, but distinct core computing operations such as the HLT (cpu sleep), MUL (integer multiplication), & FMUL (floating point multiplication) X86 instructions can be identified in each.
“Magic-touch” attack
Another variant is what the authors call a magic-touch attack. In this scenario, instead of detecting patterns in sound coming from the computer, variations in ground potential of the device can be analyzed. As with the acoustic analysis, these voltage variations in the device’s ground can be also be correlated to specific processing patterns. These ground-potential changes can be measured directly or even by simply touching the chassis with one’s hand and then measuring the variation in body potential. Another approach is to measure the ground potential on the far side of a cable that has a ground, such as a VGA cable.
I think the genie has escaped …
Rats on the West Side, bed bugs uptown
The just-released 2013 ENISA (European Union Agency for Network and Information Security) Threat Landscape report is consistent with Mick Jagger’s prescient 1978 prediction of the state of cybersecurity, captured here:
Don’t you know the crime rate
Is going up, up, up, up, up
To live in this town you must be
Tough, tough, tough, tough, tough
A number of known threats continue, attack tools are increasingly sophisticated, more nation-states are becoming proficient with these tools, and the mobile ecosystem is a ripe new battlefield. On the upside, reporting and information sharing between organizations has increased and vendor turn around in response to new vulnerabilities is faster.
I can’t give it away on 7th avenue — cheap and plentiful devices
While known to be a factor for some time, a newcomer to the threat list is the Internet of Things (IoT). IoT are networked devices that move, control, sense, surveil, video/audio, and otherwise collect and share information from and with the environment. Development tools and production for these networked devices and systems are cheap and billions more are expected in the next couple of years. (There’s even a conference preparing a road map for a trillion sensors in the next several years.)
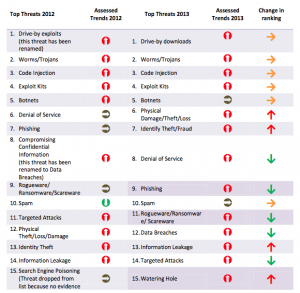
Low security is the rule rather than exception for these devices and large amounts of data are being generated. The ENISA report says, “smart environments are considered the ultimate target for cyber criminals.” For example, preliminary work for phishing attacks can be augmented by gaining information about where a victim’s smart home is, picking up information leakage from their integrated media devices (Xbox One is doing more than just playing Halo), accessing what a user’s energy usage profile might be, etc. ENISA calls out the following top emerging threats in the Internet of Things space:
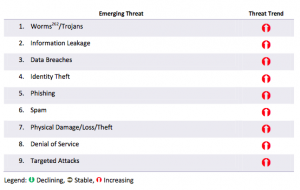 Other threats identified include:
Other threats identified include:
- Differences in many different smart appliances lead to large variances in context and content of transmitted data, opening avenues for cybercriminals.
- Devices built on embedded systems, some of which have not yet been widely deployed. Some of these embedded cores (of many different types and manufacturers) will have unknown and unpublished functions and many will be difficult to maintain (keep patched). Look at the recent D-Link saga.
- Many devices built on embedded systems do not communicate operational status to the user, eg “I am working,” “I am actively collecting data on your environment, “I am behaving erratically,” “I am off,” etc.
- Increased data creation leads to increased data storage amounts, data concentration, and corresponding increased bandwidth requirements/loads. Even a little bit of analysis can result in a significant increase in resources. Remember the basic database join (or even simpler Cartesian product) ? — you start with three elements in one list (A,B,C), but want to relate them to data in another list (D,E,F), so you relate them in a third table and you have (AD,AE,AF,BD,BE,BF,CD,CE,CF). If each element used say 1 MB of space, your initial storage and bandwidth requirement quadrupled from 6 MB (A + B + C + D + E + F) to 24 MB (A + B + C + D + E + F + AD + AE + AF + BD + BE + BF + CD + CE + CF).
For me, the other thing about Internet of Things (IoT) devices is that we often don’t really think of them as sensing, computing, analyzing, data collecting and transmitting devices. Many seem innocuous and, often, we don’t even know they’re there.
Life’s just a cocktail party
Finally, assuming that these IoT devices have already been vetted by somebody else (like the store that we bought it from) is, unfortunately, flawed logic. Businesses large and small will be rushing to market with typically insecure devices and they won’t be taking the time to analyze all of the use cases of how their product could be misused. As consumers, we need to develop the skill of thinking, ‘how could this device be misused? ‘ Most of us aren’t used to thinking like that. A family in Texas learned that the hard way a few months ago with their baby monitor. In general, if a device operates over the network and we can see it, then somebody else can see it.
Shadoobie.
[chart images from http://www.enisa.europa.eu/activities/risk-management/evolving-threat-environment/enisa-threat-landscape-2013-overview-of-current-and-emerging-cyber-threats]
Tooth tattoo
 Princeton is developing an electronic ‘tooth tattoo‘ for detecting bacteria. My money says development plans look something like this:
Princeton is developing an electronic ‘tooth tattoo‘ for detecting bacteria. My money says development plans look something like this:
- Version 1.5 sends a text to your phone telling you when to buy Altoids,
- Version 1.8 will tell you how quickly you need to buy Altoids, and
- Version 2.0 incorporates social media analysis and performs a risk analysis of likelihood of getting a date, thus potentially saving you a trip and having to get off of the couch. (Which in turn informs the Energy Conservation Module which sends you a free iTunes download and updates your thermostat.)
And she told two friends (and so on, and so on …)
The numbers and rates of growth that I’m seeing forecast for the Internet of things reminds me of that shampoo commercial in the 80’s where Heather Locklear touts the shampoo by telling two friends about how great the shampoo is. Each of those two friends in turn each tell two friends, who in turn tell two friends… and so on, and so on …
ZDNet just came out with coverage of an IDC report where the Internet-of-Things (IoT) is forecast to be a $8.9 trillion industry by 2020. 2012 spending on IoT was put at $4.8 trillion with a forecast compounded annual growth rate of 7.9%. The financial term for that, I believe, is, ‘yowza!’
The IDC report further forecasts 212 billion connected networked things by 2020 of which 30.1 billion will be autonomous connected networked things. To which an Australian might comment, ‘crikey!’
These are some big numbers. A bigger number, though, is the number of relationships, whether direct or indirect (transitive) between those things. Remember, the number of relationships in a fully-connected network grows much faster than the number of nodes. Something like:
# of nodes # of relationships
2 1 connection between them, aka relationships
3 3 relationships
4 6 relationships
5 10 relationships
.
.
.
100 4,950 relationships
.
.
.
n(n – 1)/2 is the number of relationships where n is the number of nodes or ‘things’ in IoT
Like I said, some big numbers.
and so on, and so on, and so on …
[Image: http://en.wikipedia.org/wiki/File:CA_rule30s.png]
Who’s looking at you kid? — ICS in the office
The “Internet of Things” is slowly creeping into small businesses and homes and is creating some new privacy and physical safety issues and risks.
 There has been a lot of media coverage regarding exposure of the national power grid to cyberattack. This coverage is appropriate and the risk is real. Many automated systems, aka industrial control systems or ICS, that control various aspects of electricity generation, transmission, and distribution were never intended to be controlled by Internet-connected systems. In most cases the Internet simply did not exist when the systems were installed. However, Internet-based control was added after the fact and the intersection (or collision) of two very different types of control systems — traditional industrial control and Internet-based control has created vulnerability and exposure to malicious intent. The issue is exacerbated by the fact that power systems are a high value target — successful attack and compromise can have a very big effect.
There has been a lot of media coverage regarding exposure of the national power grid to cyberattack. This coverage is appropriate and the risk is real. Many automated systems, aka industrial control systems or ICS, that control various aspects of electricity generation, transmission, and distribution were never intended to be controlled by Internet-connected systems. In most cases the Internet simply did not exist when the systems were installed. However, Internet-based control was added after the fact and the intersection (or collision) of two very different types of control systems — traditional industrial control and Internet-based control has created vulnerability and exposure to malicious intent. The issue is exacerbated by the fact that power systems are a high value target — successful attack and compromise can have a very big effect.
There are also other control systems, besides those dealing with power, that are in many buildings and increasingly in homes and small offices. These are HVAC (heating ventilation air conditioning) controls, lighting controls, security systems and others. These also have various levels of exposure to cyber attack. As an example, Google’s headquarters in Australia was recently compromised.
ICS showing up in home and office & unintended consequences
Some of these control systems that have traditionally been the domain of large buildings and complexes are making their way into homes and offices.
One example is IP-based (Internet controlled) consumer or small business security systems. These systems often provide:
- video monitoring over network/Internet
- audio monitoring over network/Internet
- sometimes 2-way audio over Internet where the person monitoring can send audio transmissions to the monitored area
 These devices are inexpensive and easily obtained at Target, Best Buy, Radio Shack or even the local drug store. They are also very vulnerable to misuse over the Internet. There was a well-publicized case last month where an IP-based (Internet-controlled) baby monitor was being used by a family in Texas. When the parents thought they heard a voice in the 2 year old child’s room, they heard a man’s voice saying horrible things to the child through the baby monitor (to include calling her by name). Someone had ‘hacked’ into the system (‘hack’ is a strong word as it was almost trivial to gain video and audio access).
These devices are inexpensive and easily obtained at Target, Best Buy, Radio Shack or even the local drug store. They are also very vulnerable to misuse over the Internet. There was a well-publicized case last month where an IP-based (Internet-controlled) baby monitor was being used by a family in Texas. When the parents thought they heard a voice in the 2 year old child’s room, they heard a man’s voice saying horrible things to the child through the baby monitor (to include calling her by name). Someone had ‘hacked’ into the system (‘hack’ is a strong word as it was almost trivial to gain video and audio access).
The parents thought that they were enhancing the child’s safety and well-being and had no idea that they were increasing risk to the child in other ways.
Assumed product sanction
There’s the rub. When these products are purchased at our local or online stores, there is this assumption of some sort of sanctioning or trust of the product by the store. Sort of like, “Target wouldn’t sell anything that would hurt me. Best Buy knows what they are selling.” This is, of course, a bad assumption.
The Internet of Things — devices and sensors talking to each other as well as humans over the Internet — opens up an exciting array of possibilities. But simultaneously it opens up a new ecosystem for misuse, privacy abuse, and even physical safety issues.
When we bring Internet-controlled devices into our office or home environments, we need to do the mental math of how the product could be misused. What would happen if it failed? What would happen if (when) an unplanned user accesses the system? Because we can be sure that someone else, that may not be well-aligned with our best interests, is doing that math.
photo credit: Argonne National Laboratory via photopin cc