LifeHacker provides a neat summary of cracking WEP and WPA Wi-Fi passwords using the BackTrack and Reaver tools. And if you can do it easily on your home or small business network, guess who else can do it easily?
LifeHacker provides a neat summary of cracking WEP and WPA Wi-Fi passwords using the BackTrack and Reaver tools. And if you can do it easily on your home or small business network, guess who else can do it easily?
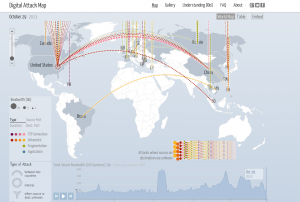
Attack map
Google and Arbor Networks have created a Digital Attack Map to show Distributed Denial of Service (DDOS) attacks in real time. The release of the map comes at the same time as Google’s release of its Project Shield using Google’s “attack mitigation technology.” The service is currently invite-only.
Because DDOS attacks are often politically or ideologically motivated, Google intends the tool to be used to assist with protection of freedom of expression.
PHP.net site is down
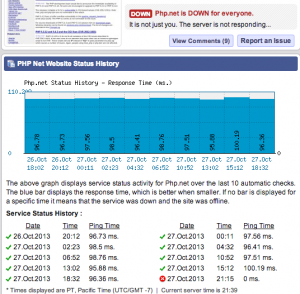 I was just getting ready to write a post about the malware on PHP.net’s servers in the past week. I went to the site to dig up some additional information and learned that it is down right now. I also got this result from isitdownrightnow.com (left).
I was just getting ready to write a post about the malware on PHP.net’s servers in the past week. I went to the site to dig up some additional information and learned that it is down right now. I also got this result from isitdownrightnow.com (left).
Per DarkReading, PHP.net says that the site served Javascript malware to some users between Oct 22 and Oct 24, 2013. There is also the possibility that the PHP.net SSL certificate private key was accessed. It has since been revoked. uk.php.net appears to be up.
Update: 10:00 pm PST: PHP.net is back up. Downtime appears to have been a little over an hour and a half.
Vulnerability found in Netgear home and small business router
 A significant vulnerability has been found in the latest version (WNDR3700v4) of Netgear’s N600 Wireless Dual-Band Gigabit Router. Per the researcher with Tactical Network Solutions that discovered the flaw, it is “trivially exploitable” and allows the attacker to disable authentication, open up a backdoor (telnet session), and then return the router to its original state so that the user never knows it was open. According to PC World, other routers may be affected as well.
A significant vulnerability has been found in the latest version (WNDR3700v4) of Netgear’s N600 Wireless Dual-Band Gigabit Router. Per the researcher with Tactical Network Solutions that discovered the flaw, it is “trivially exploitable” and allows the attacker to disable authentication, open up a backdoor (telnet session), and then return the router to its original state so that the user never knows it was open. According to PC World, other routers may be affected as well.
To mitigate the risk:
- get the latest patch from Netgear (the Shodan database still shows at least 600 unpatched routers with the WNDR3700v4 hardware revision)
- disable remote administration of the router (always)
- use strong WPA2 pass phrases
- don’t allow strangers on your network
Malware more prevalent on college campuses … Shocking!
 Dark Reading reports that universities are 300% more likely to have malware on their networks than their commercial and public sector counterparts. Given the lack of standards or hard-to-enforce standards for many of the users on campus networks, this is not a huge surprise. The academic culture of share-share-share (with some exceptions) can also contribute to this high malware prevalence. For many students and faculty, complying with a directive or guidance can be synonymous to bending down before The Man.
Dark Reading reports that universities are 300% more likely to have malware on their networks than their commercial and public sector counterparts. Given the lack of standards or hard-to-enforce standards for many of the users on campus networks, this is not a huge surprise. The academic culture of share-share-share (with some exceptions) can also contribute to this high malware prevalence. For many students and faculty, complying with a directive or guidance can be synonymous to bending down before The Man.
The Expiro family of malware is particularly prevalent in higher education. The Expiro family of malware:
- infects drives of all types — local, portable, network
- installs malicious extensions to Chrome and FireFox browsers
- attacks via web site visit “drive-bys”
- activity includes copying/stealing user names, passwords, and web histories
I don’t see top down authoritative approaches to ever to enhance security on campus. It just won’t fly. But that doesn’t mean don’t bother either. Core efforts to enhance security on campus need to include a robustly managed wired and wireless network backbone (what’s behind the wall), a lot of trust building effort with students, faculty, and staff, and a lot of education and accessible (easy to implement) guidance. This requires time and staffing (ie $$), but it is the best opportunity to tame higher ed malware rates.
[Image: Clkr.com]
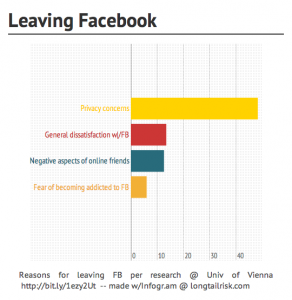
And she told two friends (and so on, and so on …)
The numbers and rates of growth that I’m seeing forecast for the Internet of things reminds me of that shampoo commercial in the 80’s where Heather Locklear touts the shampoo by telling two friends about how great the shampoo is. Each of those two friends in turn each tell two friends, who in turn tell two friends… and so on, and so on …
ZDNet just came out with coverage of an IDC report where the Internet-of-Things (IoT) is forecast to be a $8.9 trillion industry by 2020. 2012 spending on IoT was put at $4.8 trillion with a forecast compounded annual growth rate of 7.9%. The financial term for that, I believe, is, ‘yowza!’
The IDC report further forecasts 212 billion connected networked things by 2020 of which 30.1 billion will be autonomous connected networked things. To which an Australian might comment, ‘crikey!’
These are some big numbers. A bigger number, though, is the number of relationships, whether direct or indirect (transitive) between those things. Remember, the number of relationships in a fully-connected network grows much faster than the number of nodes. Something like:
# of nodes # of relationships
2 1 connection between them, aka relationships
3 3 relationships
4 6 relationships
5 10 relationships
.
.
.
100 4,950 relationships
.
.
.
n(n – 1)/2 is the number of relationships where n is the number of nodes or ‘things’ in IoT
Like I said, some big numbers.
and so on, and so on, and so on …
[Image: http://en.wikipedia.org/wiki/File:CA_rule30s.png]
D-Link begins offering router patches
D-Link announces that they are actively working to address (patch) the vulnerabilities to admin access via the web. The post also cautions against responding to unsolicited emails about security vulnerabilities that “prompt you to action” as they could be opportunistic phishing scams. They also recommend disabling wireless access to the router.
Router patches so far are available at the bottom of this D-Link post.
Patches for a separate issue involving D-Link network camera vulnerabilities are available here.
Vulnerability discovered in several D-Link wireless routers
The Register reports that a vulnerability has been discovered in several home and small business router models made by D-Link. The vulnerability allows unauthenticated users to gain administrative access to the router’s Web interface, thereby providing access to the network behind the router. Per the post, models include DIR-100, DI-524, DI-524UP, DI-604S, DI-604UP, DI-604+ and TM-G5240 units.
Because there is no current fix, users should disable admin access via wireless connection.
Not a breach, but embarrassing
Not a breach, but embarrassing.
As an example of risk of reputation damage, a group calling itself KdmsTeam has recently defaced the websites of two cybersecurity companies, Avira and AVG.
The likely approach was by taking over the domain accounts of each company via their domain registrar, Network Solutions. Domain registrars issue and manage domain names for individual or company websites. This sort of attack is sometimes referred to as DNS hijacking. Per International Business Times, KdmsTeam is a pro-Palestinian group affiliated with the hacker group Anonymous. The group also hacked the popular messaging website, WhatsApp.
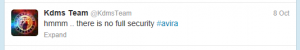
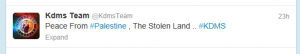
Some tweets in the past 24 hours from the group KdmsTeam:
All three sites, AVG, Avira, and WhatsApp were offline for a period of time to address the issue. All three sites are up at the time of this post.