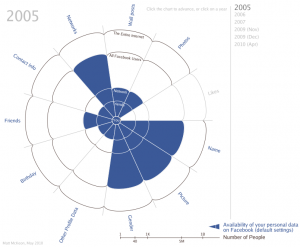
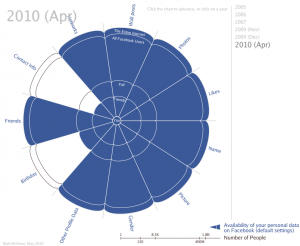
This infographic from Matt McKeon steps you through the decreased privacy in Facebook default settings between 2005 and 2010. (Click on the picture to get the years in between).
Monthly Archives: November 2013
Cyber angst art
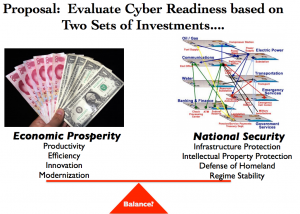
Cyber Readiness Index
- national strategy
- incident response
- ‘e-Crime’ law enforcement
- information sharing
- R&D
The index combines measures of both economic prosperity and exposure to cyber risk. For example, cybercrime, resiliency issues, identity theft, intellectual property theft, and other cyber factors are highlighted to illustrate diminished country GDP.
Some conclusions that the study draws include:
- Increase in prosperity that Internet technology and connectivity have brought over the past 30 years may not outweigh “the unreliability and riskiness caused by new threats”
- Costs of malicious cyber activity and risk must be included in a nation’s evaluation of its prosperity so that security investment can be measured
I like the approach of this index. As I suggested in my post on “Force Protection“, businesses and countries that depend on the Internet will have to redirect a real amount of its operating capacity to analyze risk and provide information security, just as the military did with personnel and physical assets in the late 70’s/early 80’s, if it is to continue to move forward.
Stuxnet revisited
While digging through the new information that came out on Stuxnet today, I came across this TED Talk given by Ralph Langner, the leading Stuxnet researcher. Though the talk is from March 2011, the content is still very informative (and it’s only 10 min long).
Tooth tattoo
 Princeton is developing an electronic ‘tooth tattoo‘ for detecting bacteria. My money says development plans look something like this:
Princeton is developing an electronic ‘tooth tattoo‘ for detecting bacteria. My money says development plans look something like this:
- Version 1.5 sends a text to your phone telling you when to buy Altoids,
- Version 1.8 will tell you how quickly you need to buy Altoids, and
- Version 2.0 incorporates social media analysis and performs a risk analysis of likelihood of getting a date, thus potentially saving you a trip and having to get off of the couch. (Which in turn informs the Energy Conservation Module which sends you a free iTunes download and updates your thermostat.)
2014 attacks to be highly targeted & well-researched
Security provider Websense says that while the volume of attacks will decrease, there will be an increased use of highly targeted, well-researched attacks. These attacks, in turn, will be used as a stepping stone for subsequent malicious activity after stealing user credentials.
The firm also predicts that a major data-destruction attack will occur in 2014. Further, according to this Websense report (and with the caveat that the firm sells related services), there will be an increase of related ransomware attacks in SMB’s. Other predictions include ongoing Java exploits, increased focus on attacking data in the cloud, and increased reconnaissance activity on executives via professional social networks such as LinkedIn. The report also speculated increased attacks on the vendors and contractors of large companies with the thought being that these ‘support’ companies will have less sophisticated cyber defenses than their larger partners.
More small businesses doing their own technical support
 An 800 participant survey conducted by the National Small Business Association shows more small businesses are managing their own IT and web sites. Other differences noted between the 2013 survey and a similar survey conducted in 2010 include:
An 800 participant survey conducted by the National Small Business Association shows more small businesses are managing their own IT and web sites. Other differences noted between the 2013 survey and a similar survey conducted in 2010 include:
- desktop usage grew by 11% (76% to 87%)
- laptop usage grew by 17% (67% to 84%)
- smartphone usage grew by 17% (57% to 74%)
- growth in businesses allowing telecommuting – 16% (44% – 60%)
- online bank account management grew by 10% (73% – 83%)
Notably there was a 12% drop in businesses using external service providers for technical support and a 15% increase in business owners providing their own technical support. Similarly, there was an 11% drop in companies paying external providers for web support accompanied by an 18% increase in owners that do it themselves. (I’m guessing WordPress and other blog frameworks had a lot to do with that.) Social media presence also grew substantially with LinkedIn leading with a 20% increase.
Tis the season
 From the SANS Institute, things to look out for while shopping online this season:
From the SANS Institute, things to look out for while shopping online this season:
Fraudulent website indicators:
- no phone # for sales or support
- website domain name is different from the domain name on company email and contact info
- poor grammar and/or spelling on website
- the website seems to be an exact replica of what you have used in the past, but the domain name is slightly different
Your computer’s hygiene:
- current AntiVirus running
- autoupdate on operating system
- one account per user
- different passwords for different sites
- on a trusted network (one you run w/remote admin turned off)
Payment:
- credit cards are better than debit cards
- review your statements at least monthly
- turn on alerts on your credit cards if available
Scams and fake sites will be blossoming this holiday season, so be on your toes ..
[shopping cart image: clker.com]
Risk-based authentication as alternative to chronically problematic password paradigm
 Authentication, the process of trying to prove that you are who you say you are to an online system, has primarily been driven by user ID’s, aka logins or user names, and an accompanying password. In theory, the password is secret, only known by the user associated with it, and thereby by able to authenticate or provide proof of identity. The problem is that there are a plethora of flaws to that. Some of these include:
Authentication, the process of trying to prove that you are who you say you are to an online system, has primarily been driven by user ID’s, aka logins or user names, and an accompanying password. In theory, the password is secret, only known by the user associated with it, and thereby by able to authenticate or provide proof of identity. The problem is that there are a plethora of flaws to that. Some of these include:
- the password is not secret because the user shared it with someone else
- the password is not secret because the user wrote it down on a yellow sticky note & stuck it to their monitor at work or school
- the password is guessable and could be figured out if there were readily available, free password cracking tools available online
- there are a million readily available, free password cracking tools available online
- a password hacked on one site is used on another user site — because users use the same password across multiple different accounts & sites because it’s very hard to remember different complex passwords for many different accounts and sites
- and on and on
An alternative is a newer approach that computes a risk score that is associated with login attempts (the authentication process). A usage profile is developed based on several factors:
- user ID
- user device
- geographic location
- target system (what they’re trying to log onto)
- time of day they typically log in
- their IP address
- typing speed
A user that tends to log into their company’s database on weekdays at a particular time of day from a particular workstation will generate a baseline profile. An attempt to login to that database Sunday morning from a mobile device will generate a disparity. This will signal the need for additional proof of identity (maybe a phone call or PIN) or perhaps disable the login entirely.
It seems some time in use and data to analyze effectiveness is called for, but if that looks good, this is pretty cool. More here. Even Bruce Schneier likes it!
The roof the roof the roof is on fire
Reminiscent of the delicate lyrics of Rock Master Scott and the Dynamic Three, there’s a lot of press about a number of different attacks right now on individuals, SMB’s, and large enterprises. CryptoLocker ransomware, a Microsoft attack via images, and the oldie-but-goodie of continued Java vulnerabilities. It seems that the attacks are coming from all sides. And I believe they are.
The CryptoLocker attack seemed interesting and fairly novel a few weeks ago, but I figured it would fade away pretty quickly as new anti-virus signatures or other patches caught up with it. However, it appears to be on the rise. CryptoLocker is a form of malware known as ransomware where the attacker encrypts your files and then demands a ransom for the key to unlock the files. There have been reports of successful file unlocks after paying ransom, no file unlock after paying ransom, and also of the ransomware actor extending the due date. US Cert has issued an alert regarding the rise in infections.
And then Microsoft has issued a security advisory regarding vulnerabilities in its graphics component and malicious TIFF files. Apparently, malicious code hidden in an image can execute and do arbitrary things. So we’ve got that going for us. Affected systems include Office 2003, 2007, 2010, Server 2008, and Lync. Microsoft offers a fixit/workaround here.
Finally, rounding out the happy news is the update from a Kaspersky report that there were over 14 million attacks with Java exploits between 9/2012 and 8/2013, with more than 8 million of those in the second half of that period. While chasing down some Java issues across several hundred machines myself last week, I counted over 200 Java fixes in the past year and that’s not counting new ‘features’.
It’s been said before, but the good guys are not winning this battle. The general consensus is that it’s getting worse, not better. What to do? While no panacea, the basics apply — current anti-virus with daily updates, autoupdate on operating systems, good Internet hygiene — don’t open unknown mail, don’t download unknown things, keep a watchful eye for phishing attacks, use good passwords and don’t share them. I think this will be our best/only approach for some time to come.