Cloud services and social media services are often touted as a way for Small to Medium-sized Businesses (SMB’s) to manage their IT needs, information risk, and information security needs. While there is real potential for SMB’s in this space, it is not without risk. As an example, CyberSquared has documented increasing use of attackers using trusted cloud services such as Dropbox & WordPress to manage aspects of an attack.
Sophisticated, Chained Multi-component Attacks
A recent attack had these sophisticated components:
- A Word document with embedded malicious content that would attempt to activate upon opening.
- The content of the Word document was relevant to the recipients of the attack. In this case it appears to be a policy document for the Association of Southeast Asian Nations (ASEAN). That is, it’s a document that targeted recipients would likely be interested in opening.
- There was also evidence that the Word document was a product/artifact of an earlier attack. That is, data/documents/information collected/stolen from earlier attacks are used as components and tools for future attacks.
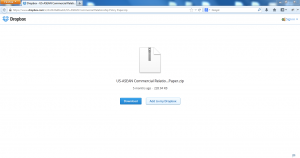
- The document was put in a Dropbox account created quickly and at no charge by the attacker.
- The attacker then emailed the Dropbox account info to the targeted recipients.
- Now for some extra sneakiness — note that the file says that it’s a zipped (compressed file) with the .zip extension. Upon opening, researchers saw that it used a fake Adobe pdf icon to cover up the fact that it was actually a Word document (that had the malicious code).
- Once a user received this Dropbox link and opened the compressed-faux-pdf-actual-malicious-Word-doc file, the next phase would start. From here the malicious code would then contact a WordPress site to get Command & Control information so that it could get specific instructions to further its attack.
- Note IP address and port information embedded in an otherwise seemingly innocuous post.
Advantages of a Trusted Public Service to Attackers
- Attackers can hide behind a trusted brand name such as Dropbox, WordPress, or Twitter
- Ease of attacker anonymity stems from ease of account set up
- Attackers able to use cloud service infrastructure to target victims, eg using Dropbox email component to reach out
- Malicious content easily bypasses old school detection mechanisms
This is some pretty sneaky stuff embedded into some trusted services that often market directly to SMB’s. I’m not saying don’t use them — they do offer huge convenience and direct cost savings. However, it is critical to recognize that they don’t offer a slam-dunk solution for security. Indeed, no solution offers this. Like everything else, reflection on risk needs to occur to ensure an SMB has the best chance for good decisions.