While digging through the new information that came out on Stuxnet today, I came across this TED Talk given by Ralph Langner, the leading Stuxnet researcher. Though the talk is from March 2011, the content is still very informative (and it’s only 10 min long).
Tag Archives: SCADA
Who’s looking at you kid? — ICS in the office
The “Internet of Things” is slowly creeping into small businesses and homes and is creating some new privacy and physical safety issues and risks.
 There has been a lot of media coverage regarding exposure of the national power grid to cyberattack. This coverage is appropriate and the risk is real. Many automated systems, aka industrial control systems or ICS, that control various aspects of electricity generation, transmission, and distribution were never intended to be controlled by Internet-connected systems. In most cases the Internet simply did not exist when the systems were installed. However, Internet-based control was added after the fact and the intersection (or collision) of two very different types of control systems — traditional industrial control and Internet-based control has created vulnerability and exposure to malicious intent. The issue is exacerbated by the fact that power systems are a high value target — successful attack and compromise can have a very big effect.
There has been a lot of media coverage regarding exposure of the national power grid to cyberattack. This coverage is appropriate and the risk is real. Many automated systems, aka industrial control systems or ICS, that control various aspects of electricity generation, transmission, and distribution were never intended to be controlled by Internet-connected systems. In most cases the Internet simply did not exist when the systems were installed. However, Internet-based control was added after the fact and the intersection (or collision) of two very different types of control systems — traditional industrial control and Internet-based control has created vulnerability and exposure to malicious intent. The issue is exacerbated by the fact that power systems are a high value target — successful attack and compromise can have a very big effect.
There are also other control systems, besides those dealing with power, that are in many buildings and increasingly in homes and small offices. These are HVAC (heating ventilation air conditioning) controls, lighting controls, security systems and others. These also have various levels of exposure to cyber attack. As an example, Google’s headquarters in Australia was recently compromised.
ICS showing up in home and office & unintended consequences
Some of these control systems that have traditionally been the domain of large buildings and complexes are making their way into homes and offices.
One example is IP-based (Internet controlled) consumer or small business security systems. These systems often provide:
- video monitoring over network/Internet
- audio monitoring over network/Internet
- sometimes 2-way audio over Internet where the person monitoring can send audio transmissions to the monitored area
 These devices are inexpensive and easily obtained at Target, Best Buy, Radio Shack or even the local drug store. They are also very vulnerable to misuse over the Internet. There was a well-publicized case last month where an IP-based (Internet-controlled) baby monitor was being used by a family in Texas. When the parents thought they heard a voice in the 2 year old child’s room, they heard a man’s voice saying horrible things to the child through the baby monitor (to include calling her by name). Someone had ‘hacked’ into the system (‘hack’ is a strong word as it was almost trivial to gain video and audio access).
These devices are inexpensive and easily obtained at Target, Best Buy, Radio Shack or even the local drug store. They are also very vulnerable to misuse over the Internet. There was a well-publicized case last month where an IP-based (Internet-controlled) baby monitor was being used by a family in Texas. When the parents thought they heard a voice in the 2 year old child’s room, they heard a man’s voice saying horrible things to the child through the baby monitor (to include calling her by name). Someone had ‘hacked’ into the system (‘hack’ is a strong word as it was almost trivial to gain video and audio access).
The parents thought that they were enhancing the child’s safety and well-being and had no idea that they were increasing risk to the child in other ways.
Assumed product sanction
There’s the rub. When these products are purchased at our local or online stores, there is this assumption of some sort of sanctioning or trust of the product by the store. Sort of like, “Target wouldn’t sell anything that would hurt me. Best Buy knows what they are selling.” This is, of course, a bad assumption.
The Internet of Things — devices and sensors talking to each other as well as humans over the Internet — opens up an exciting array of possibilities. But simultaneously it opens up a new ecosystem for misuse, privacy abuse, and even physical safety issues.
When we bring Internet-controlled devices into our office or home environments, we need to do the mental math of how the product could be misused. What would happen if it failed? What would happen if (when) an unplanned user accesses the system? Because we can be sure that someone else, that may not be well-aligned with our best interests, is doing that math.
photo credit: Argonne National Laboratory via photopin cc
Hacking the Internet of Things
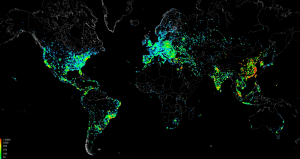
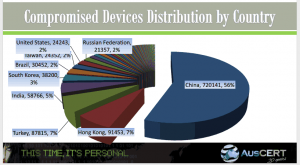
A research botnet was created to detect and compromise unprotected embedded control devices. These embedded control devices can be found in industrial control systems, medical devices, home appliances, and similar. A botnet is created when multiple devices are attacked, compromised (aka ‘owned’), and subsequently controlled by the attacker. The botnet was named Carna Botnet after the Roman goddess of the protection of vital organs and health.
- Unprotected embedded devices (tiny computers that typically control things) detected at rate of 1 every 5 minutes
- Discovered millions of unprotected devices, eg no or trivial username & password.
- Carna Botnet now 1.2 million compromised devices
- Of that 1.2 million, 420,000 have sufficient functionality & resources to continue to propagate the botnet
The initial report is here. Presentation here.
As the world continues to control more and more with networked embedded devices, ie the Internet of Things, we can expect a global rapidly growing platform for malicious behavior that we will need to attend to.
Risk Managing Residual Old-School Devices
I’ve encountered this risk discussed in this Forbes article more than once when taking over an organization and doing an initial information risk assessment. People tend to forget that these embedded devices can have simple or full fledged Linux distributions (or other OS) in the firmware. Also, the default ports that were left open can be eye opening.