Rapid growth brings many good things, but also drives how we manage risk. [Image: theconnectivist.com http://bit.ly/1owv1dp]
IoT devices as attack enablers
In all of the hoopla and coolness and excitement of the Internet of Things, we can sometimes forget the underlying subtle and amazing thing that they are all networked computing devices, many with well known and well understood operating systems. So, for a moment, forget that cool thing that the IoT device does in its local environment (capture video, audio, biometric authentication information, health information, temperature, humidity, refrigerator status, air composition, etc) and just remember that they are networked computing devices — many of these with substantial computing resources.
What this means is that IoT devices are not just targets themselves, but can also act as attack enablers or attack platforms. This can occur via direct hack or by unwitting participation in a botnet.
From this recent analysis of a 2008 Turkish pipeline hack and sabotage:
“As investigators followed the trail of the failed alarm system, they found the hackers’ point of entry was an unexpected one: the surveillance cameras themselves.
The cameras’ communication software had vulnerabilities the hackers used to gain entry and move deep into the internal network, according to the people briefed on the matter.
Once inside, the attackers found a computer running on a Windows operating system that was in charge of the alarm-management network, and placed a malicious program on it. That gave them the ability to sneak back in whenever they wanted.”
So, the networked computing presence of the cameras themselves were used as a stepping stone (aka attack point) into the larger network. Some weakness in the operating system (OS) of the camera devices themselves provided a point of entry (‘vector’ in geek speak) into the pipeline’s operational network.
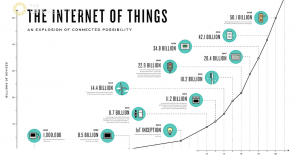
Big numbers
So, if we look at the growth in the number of IoT devices and consider them, for now, only as networked computing devices capable of being compromised, that’s a lot of new stepping stones for attacks.
These growing number of devices can enable & assist attacks by:
1) providing many more attack platforms, which …
2) provides more opportunities for indirection in attack, which …
3) makes attribution more difficult
 Let’s get transitive – Kauffman’s buttons
Let’s get transitive – Kauffman’s buttons
At the risk of being a little bit tangential, all this reminds me of another network phenomenon, dealing with botnets, that I believe occurs. It is one that is exacerbated by the rapid increase in networked computing nodes, eg from IoT growth and has to do with how quickly the character of a network can change under fairly simple conditions.
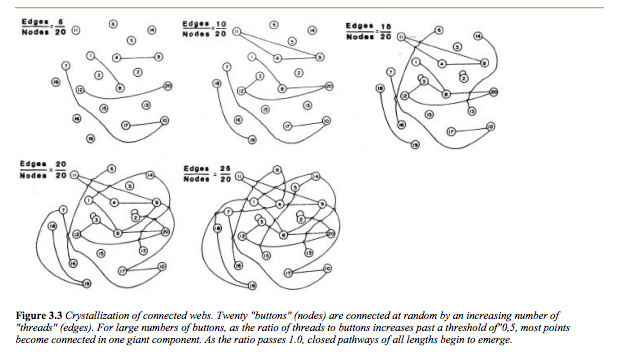
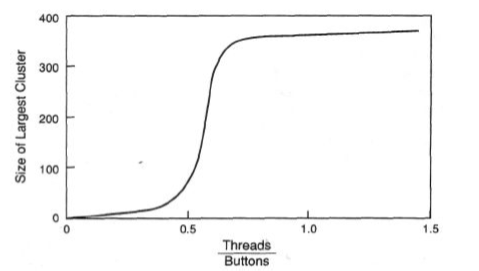
I’ve always been intrigued with this ‘toy problem’ that Stuart Kauffman describes in his book, At Home in the Universe. He says to imagine that you have a bunch of buttons on the floor and some pieces of thread. You arbitrarily pick two buttons and then connect them with a piece of thread, a button at each end. Then you arbitrarily pick two more buttons and connect those two. (The original buttons are not excluded; they are still contenders. ) Keep doing this. While doing so, create a graph and plot the thread to number of buttons ratio on the X axis and the size of the largest cluster on the Y axis.
Not too much happens at first. Early on, the largest button cluster stays pretty small. Then, at a certain point, the size of the largest cluster leaps. Logically, it’s not surprising. You can see how it happens. However, I still find myself staring at that big jump. That’s a real phase change for at least one aspect of that button network.
I think a similar thing happens with some botnets, particularly P2P botnets, as they grow in size. We can make the reasonable assumption that some botnet sizes are more effective than others at carrying out their varied nefarious tasks, eg 1000 is probably better than 10. While individual bots in botnets do not connect to all of the other bots on the network, they do connect to many.
IoT growth => More buttons
In this environment, I think Kauffman’s toy problem still applies. Namely, at some point, the largest cluster size grows very rapidly. Maybe not with the near-vertical drama of Kauffman’s problem where everything can be connected, but still with a significant acceleration in growth of the largest cluster once a critical point is reached. And if the largest cluster size suddenly meets or exceeds that putative optimal botnet size, well then, we’ve got ourselves an effective botnet.
So if the rapid growth in IoT provides many more buttons, then there are also many more buttons/potential botnet participants for the network. And the fact that these botnets can fairly suddenly (aka seemingly arbitrarily) reach their optimal effectiveness adds another air of uncertainty and difficult-to-predictness to the whole thing.
Not gloom & doom, but evolving risk picture
The sky is not falling and the Internet of Things holds much promise, but the way we look at risk will need to change. The advent and rapid growth of the Internet of Things will change some of the math on the Internet. More botnets will come online and they will do so in unpredictable ways. I’m not saying the end is near, but rather the way we look at risk will have to change.