Developing a market for cybersecurity insurance is more difficult than it may seem. With a rise in business losses stemming from malicious activities and adverse events in the cyber world, creating a market for cybersecurity insurance where losses could be mitigated would seem to be a no brainer. However, developing, maturing, and establishing trust in a cybersecurity insurance market is slow in coming.
What it’s supposed to do
Ostensibly, implementation of a mature cybersecurity insurance market can provide protection and mitigation for such events as:
- data breach
- network damage
- cyber extortion
- brand damage
- financial loss
- other
The Department of Homeland Security quotes the Department of Commerce in describing cybersecurity insurance as an “effective, market-driven way of increasing cybersecurity.” The idea is that cybersecurity provides mitigation to damages suffered from a cyber event and also enhances cybersecurity in general by motivating better information risk management and security via premium discounts for good practices.
Implementation and chicken and egg challenges
Despite the seemingly obvious benefits, cybersecurity insurance has yet to undergo wholesale adoption. DHS and the May 2013 Cyber Risk Culture Roundtable Readout Report hosted by the National Protection & Programs Directorate (NPPD) offer some reasons for lack of adoption to date:
- Cost — An added cost that companies must deal with plus the perception of cybersecurity insurance as a luxury item
- Uncertainty — potential customers wonder whether carriers will actually payout on cyber event claims. There is little current precedent for such claims and payouts, hence the chicken and egg problem
- High risk appetites — Particularly in technology fields where there is a lot of entrepreneurship, the tolerance for risk is high
- Market/services maturity — Awareness and incentives structures within the cybersecurity insurance industry are not ubiquitous
- Lack of clarity/precedence/data on likelihood of an adverse cyber event
- Confusion/misunderstanding on exactly what is covered with cybersecurity insurance
At the cybersecurity framework hearing held by the Senate Commerce, Science, and Transportation Committee on July 25, 2013, Patrick Gallagher, Director of U.S. Department of Commerce’s National Institute of Standards and Technology (NIST) also suggested that the cybersecurity insurance market was not yet sufficiently mature to handle large-scale, catastrophic cyber events. Dr. Gallagher stated that there was not yet a robust actuarial and monetized basis for such large-scale coverage.
Further, at the same hearing, CEO of RSA, Art Coviello suggested that developing an actuarial basis for adverse cyber events was particularly difficult because the computing environment is changing so rapidly and because of the vast amount of data being generated that needs some form of analysis in order to determine appropriate coverage.
As much as I want to encourage and contribute to the rapid development of a mature cybersecurity insurance market, I too have concerns about how policies are written, how cyber events are described, and how much work is required to get an actual payout on a claim. To get consumer buy-in in the short term, insurance providers might have to ‘go long’ with claims and payouts to establish trust and confidence amongst consumers.
Would you purchase cybersecurity insurance? What sorts of events would you like protection from? Data breach? Data loss or theft? What changes/implementations would make purchasing cybersecurity insurance more appealing to you?
[image: commons.wikimedia.org/wiki/File%3AForgotten_umbrella.jpg]






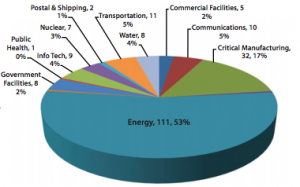
![What's one more fish? (Image by Earth'sbuddy [CC-BY-SA-3.0] via Wikimedia Commons](http://longtailrisk.com/wp-content/uploads/2013/07/Salmon-150x150.jpg)