Monthly Archives: June 2013
SMB Information Risk & Security — A Tragedy of the Commons?
Do small and medium sized businesses (SMB’s) erode their common resource, the Internet, by not making an investment in managing information risk and security in their own operations?
Garrett Hardin (1915-2003) introduced the idea of individual actors depleting a common resource in his 1968 paper published in Science entitled The Tragedy of the Commons. The idea is that individuals, making use of a common resource, will make decisions in their own interest to the detriment of the the group as a whole — even knowing that they are a part of that same group that will suffer.
Overfishing
A classic example is overfishing an area. In theory, all of the individuals fishing know that if they catch more than X fish in a certain period of time that they are contributing to the permanent depletion of that resource — which ultimately affects them. However, when thinking for themselves, they think, ‘if I don’t get that extra fish, someone else will. So it might as well be me.’
 Another example is multiple farmers with cows grazing on the same common pasture. Some number of total cows is sustainable and the grass will regrow in time to continue feeding all of the cows. Beyond that point, the pasture will degrade until it is eventually totally consumed. While overgrazing is detrimental to all, each individual farmer thinks, ‘if I don’t maximize this and put more cows on the field, I’ll suffer in the short term — I’m not even thinking about the long term. I’m just trying to keep up with or beat the farmer next to me this week.’ As a result, the resource becomes completely depleted.
Another example is multiple farmers with cows grazing on the same common pasture. Some number of total cows is sustainable and the grass will regrow in time to continue feeding all of the cows. Beyond that point, the pasture will degrade until it is eventually totally consumed. While overgrazing is detrimental to all, each individual farmer thinks, ‘if I don’t maximize this and put more cows on the field, I’ll suffer in the short term — I’m not even thinking about the long term. I’m just trying to keep up with or beat the farmer next to me this week.’ As a result, the resource becomes completely depleted.
Hope on the horizon?
Elinor Ostrom (1933-2012) received the Nobel Prize for her work showing that in many systems with a common resource, individuals communicate with each other and develop working relationships such that the resource is not depleted. More on her work in a subsequent post.
Internet as Common Pool Resource (CPR)
It’s not hard to draw the analogy of Internet as common resource for SMB’s (as well as large enterprises and consumers). When a company connects to the Internet, it is participating in that resource. It gets value from the resource. It also has the potential to harm the resource, and in effect, deplete the resource.
Large enterprises have more resources available for risk management and security activities and can be more motivated to protect their own investments. I would hazard a guess that, on average, SMB’s have more risk tolerance than most large established enterprises.
When an SMB is attacked or ‘compromised’, a couple of things can happen: 1) the SMB suffers financial or reputation loss or both, and/or 2) the SMB’s resources (computers) are used as assets to attack the computers of other businesses. This weakens, or depletes, the community resource.
SMB’s typically have less resources when compared to their large enterprise counterparts. It’s a hard decision to divert limited cash from marketing, production, and R&D to spend it on information risk management and security. However, not making an investment in security and risk management, significantly exposes themselves as well as the common pool resource of the Internet to harm.
So whose responsibility is it? SMB’s represent a large portion of the workforce, with each workforce member potentially with one or many computing devices. If SMB’s aren’t motivated to invest in risk management and security, this means that a substantial part of the economy is operating while poorly protected.
Should SMB’s be held accountable if their computers are hacked and then used to attack other computers? Should SMB’s have a minimum standard for computing devices, to include smartphones? Would this stifle innovation? Should trade organizations establish standards? The government?
Or, do SMB’s simply represent a tragedy of the commons?
Adm Mike Mullen at Gartner Summit
What keeps Adm Mike Mullen up at night — from Gartner Risk & Security Summit 2013 keynote:
- National debt
- K-12 education system
- Political paralysis
- Cyber vulnerability, threats, and infrastructure
- Veterans health, education, & employment (1000 veterans leaving service every day, but only 100 being hired everyday)
More on cyber —
- Adm Mullen went on to say that cyber risk is primary existential threat (ie potential to change way of life) to US.
- Calls partnership between presidents Obama and Xi most important bilateral relationship in world
- Restated his belief in the assumption of breach approach to information security
- On accountability, concerned accountability is not clear in cyber world. Wants to see leadership and accountability in social networking world.
IT Risk Management Lessons Learned
From Tom Scholtz’s presentation at Gartner Security & Risk Summit 2013 on lessons learned in IT Risk Management:
- Understand that there is a limited appetite for risk management as a topic by business users (ie, don’t overdo it)
- Ideally, risk assessment is performed on business processes (vs IT assets or services)
- Risk interpretation is personal — there is no correct answer
- Don’t try to use only one risk assessment method for all assessment scenarios — one size does not fit all
- Don’t use security & risk operational metrics when communicating risk to leadership — convert them to business objectives
- Risk affinity for individuals and organizations changes over time
- In many IT risk cases, quantitative risk analysis is impossible (because of lack of relevant actuarial data)
- In the quest to simplify, don’t try to roll up multiple independent risks into one metric
- Always link risk management activities to business objectives
- Focus on risks that we can do something about
Finally, while possibly an unpopular sentiment amongst some practitioners, risk should be treated more like an art than science, where the focus is on gaining and documenting experience* and continuous improvement. *(See my post Inverting Sun Tzu).
Download page added — risk worksheets & templates for SMB’s (from posts)
Added downloadable information risk worksheets, forms, & templates for SMB’s from posts
Meet the New Boss … Reincarnated malware returns to SMB’s
Same as the old boss …
A popular form of malware called ZeuS/Zbot has made a comeback and SMB’s are particularly at risk. Initially identified in 2007, the malware typically steals user credentials for banking activity. SMB’s have higher risk exposure because they typically don’t have the resources for risk and security programs. One SMB, a Maine construction company, was robbed of almost $600,000 in 2009.
ZeuS/Zbot source code is known to be readily available on underground informal networks as well as, apparently, even available for sale.
Back because it works
Once thought to be largely eradicated, ZeuS/ZBot is back because of market analysis and software upgrades. SMB’s typically have a richer target (bigger accounts) than individuals and are also generally less protected than larger businesses. Facebook is also providing a new and effective ‘attack vector’ for getting the malware onto user computers to steal data.
How does it work ?
ZeuS/Zbot uses a ‘Man-In-The-Browser’ (MITB) attack. Once a machine is infected, Zbot is able to monitor web activity and watch for particular banking sites. User credentials are copied and replicated on a database maintained by the attacker. With this information, attackers or their proxies (‘mules’) can login and transfer money wherever they’d like. By downloading a configuration file established by the attacker, the list of banking sites can be updated.
Prevention/due care activity for SMB’s includes:
- Move banking activity to dedicated machines used for no other purpose than banking
- Educate employees on threats, risks, and behavior
- Review high risk accounts (eg big balances) and access/authorization to them
- Keep antivirus/antimalware software current
- Implement a simple information risk management plan (Shocking!)
What percentage of your computers have current antivirus scanning? How do you know?
Default Passwords
Why is it important to change default passwords on hardware, applications, and other systems? Because the passwords are published and, in effect, not passwords at all. A few responses from Googling ‘default passwords’ :
And there’s plenty more.
Lesson:
Default password = No password
FIS Spends Over $100 million in Breach Response
Fidelity National Information Services (FIS), a large banking services company, was hacked in 2011 and information from that breach was used in a $13 million ATM theft. Initial reports said damage was limited to a small portion of its organization. Subsequent audit reveals a much larger breach plus apparently poor management of its incident response.
- More than $100 million spent in response to breach
- An FDIC audit showed that since the breach & response that many machines still have default, no, or poor passwords
- An FDIC vulnerability scan found over 10,000 instances of default passwords in use
- FDIC report in November 2012 shows 18,747 network vulnerabilities and 291 application vulnerabilities presented as past due
More here
Poorly Defended & Under Attack — SMB’s in the Spotlight
Cyberattacks on Small and Medium-sized Businesses (SMB) continue to grow, causing damage to the individual SMB’s as well as the international business network infrastructure itself.
Why attack SMB’s ?
SMB’s are under increasing attack for several reasons:
- They are often poorly defended because of resource constraints
- The are typically connected to other SMB’s and larger organizations, providing an attack path (or ‘attack vector’) to other businesses
- There are a lot of them
Simply because of their size, SMB’s are typically poorly defended because they are resource constrained and don’t have the IT and/or security expertise on staff.
A recent UK survey showed only 14% of SMBs thought that cyber security threats were of highest priority and felt that they had sufficient skills and resources in place to manage the threat. In another study commissioned by Microsoft, AMI-Partners found that of Involuntary IT Managers (non-technical staff assuming technical duties) surveyed:
- 30% thought IT management was a nuisance
- 26% did not feel qualified to manage IT
- 60% wanted to simplify their organizations IT systems to make their management more feasible
The AMI-Partners survey was of 538 Involuntary IT Managers across 5 countries in companies of 100 employees or less. The survey also found an aggregate loss of over $24 billion due to inefficiencies stemming from the Involuntary IT Manager not performing their primary job duty.
Another reason for targeting SMB’s is that their interconnectivity with other businesses can provide an attack path to larger businesses.
Finally, there are a lot of SMB’s . In industrialized countries, a few very large companies live side by side with many small and medium-sized companies.
What to do about information security and risk management in SMB’s ?
That, then, is the question. The resource constraints that SMB’s face aren’t going to magically disappear anytime soon. Should the government assist? Or conversely, should that security and risk management be a cost of doing business for the SMB? Should SMB’s face penalties for insecure environments or poor infrastructure support practices? Will that stifle innovation?
I lean towards a hybrid solution where the SMB is responsible for knowledge and awareness of itself and its information risks, but I would like to see the government make resources available to SMB’s (or support industry groups to do the same). These resources could include:
- simple guidelines and minimum configuration standards. (Some of the current policies and directives are so convoluted and difficult to read as to be impossible to implement.)
- simple asset inventory tools
- network mapping tools that assist SMB’s with self-documentation
- simple penetration test tools coupled with results analysis tools
- simple risk management tools
SMB’s themselves, professional organizations/networks, or governments must find a way to better educate and prepare SMB’s.
- How do you think SMB’s should manage their IT & Information Management systems?
- What do you do to protect your business?
- Do you actively manage information risk?
- Do you turn it over to someone else?
- How well do you understand your exposure to cyber attack and compromise?
- Do you avoid altogether because it’s simply overwhelming?
Hacking the Internet of Things
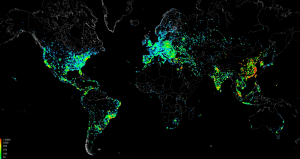
A research botnet was created to detect and compromise unprotected embedded control devices. These embedded control devices can be found in industrial control systems, medical devices, home appliances, and similar. A botnet is created when multiple devices are attacked, compromised (aka ‘owned’), and subsequently controlled by the attacker. The botnet was named Carna Botnet after the Roman goddess of the protection of vital organs and health.
- Unprotected embedded devices (tiny computers that typically control things) detected at rate of 1 every 5 minutes
- Discovered millions of unprotected devices, eg no or trivial username & password.
- Carna Botnet now 1.2 million compromised devices
- Of that 1.2 million, 420,000 have sufficient functionality & resources to continue to propagate the botnet
The initial report is here. Presentation here.
As the world continues to control more and more with networked embedded devices, ie the Internet of Things, we can expect a global rapidly growing platform for malicious behavior that we will need to attend to.