Almost 5 million LinkedIn clear text passwords in a lovely bound set for your viewing and sharing pleasure. So we’ve got that going for us.

Security provider Websense says that while the volume of attacks will decrease, there will be an increased use of highly targeted, well-researched attacks. These attacks, in turn, will be used as a stepping stone for subsequent malicious activity after stealing user credentials.
The firm also predicts that a major data-destruction attack will occur in 2014. Further, according to this Websense report (and with the caveat that the firm sells related services), there will be an increase of related ransomware attacks in SMB’s. Other predictions include ongoing Java exploits, increased focus on attacking data in the cloud, and increased reconnaissance activity on executives via professional social networks such as LinkedIn. The report also speculated increased attacks on the vendors and contractors of large companies with the thought being that these ‘support’ companies will have less sophisticated cyber defenses than their larger partners.
 An 800 participant survey conducted by the National Small Business Association shows more small businesses are managing their own IT and web sites. Other differences noted between the 2013 survey and a similar survey conducted in 2010 include:
An 800 participant survey conducted by the National Small Business Association shows more small businesses are managing their own IT and web sites. Other differences noted between the 2013 survey and a similar survey conducted in 2010 include:
Notably there was a 12% drop in businesses using external service providers for technical support and a 15% increase in business owners providing their own technical support. Similarly, there was an 11% drop in companies paying external providers for web support accompanied by an 18% increase in owners that do it themselves. (I’m guessing WordPress and other blog frameworks had a lot to do with that.) Social media presence also grew substantially with LinkedIn leading with a 20% increase.
 Authentication, the process of trying to prove that you are who you say you are to an online system, has primarily been driven by user ID’s, aka logins or user names, and an accompanying password. In theory, the password is secret, only known by the user associated with it, and thereby by able to authenticate or provide proof of identity. The problem is that there are a plethora of flaws to that. Some of these include:
Authentication, the process of trying to prove that you are who you say you are to an online system, has primarily been driven by user ID’s, aka logins or user names, and an accompanying password. In theory, the password is secret, only known by the user associated with it, and thereby by able to authenticate or provide proof of identity. The problem is that there are a plethora of flaws to that. Some of these include:
An alternative is a newer approach that computes a risk score that is associated with login attempts (the authentication process). A usage profile is developed based on several factors:
A user that tends to log into their company’s database on weekdays at a particular time of day from a particular workstation will generate a baseline profile. An attempt to login to that database Sunday morning from a mobile device will generate a disparity. This will signal the need for additional proof of identity (maybe a phone call or PIN) or perhaps disable the login entirely.
It seems some time in use and data to analyze effectiveness is called for, but if that looks good, this is pretty cool. More here. Even Bruce Schneier likes it!
Reminiscent of the delicate lyrics of Rock Master Scott and the Dynamic Three, there’s a lot of press about a number of different attacks right now on individuals, SMB’s, and large enterprises. CryptoLocker ransomware, a Microsoft attack via images, and the oldie-but-goodie of continued Java vulnerabilities. It seems that the attacks are coming from all sides. And I believe they are.
The CryptoLocker attack seemed interesting and fairly novel a few weeks ago, but I figured it would fade away pretty quickly as new anti-virus signatures or other patches caught up with it. However, it appears to be on the rise. CryptoLocker is a form of malware known as ransomware where the attacker encrypts your files and then demands a ransom for the key to unlock the files. There have been reports of successful file unlocks after paying ransom, no file unlock after paying ransom, and also of the ransomware actor extending the due date. US Cert has issued an alert regarding the rise in infections.
And then Microsoft has issued a security advisory regarding vulnerabilities in its graphics component and malicious TIFF files. Apparently, malicious code hidden in an image can execute and do arbitrary things. So we’ve got that going for us. Affected systems include Office 2003, 2007, 2010, Server 2008, and Lync. Microsoft offers a fixit/workaround here.
Finally, rounding out the happy news is the update from a Kaspersky report that there were over 14 million attacks with Java exploits between 9/2012 and 8/2013, with more than 8 million of those in the second half of that period. While chasing down some Java issues across several hundred machines myself last week, I counted over 200 Java fixes in the past year and that’s not counting new ‘features’.
It’s been said before, but the good guys are not winning this battle. The general consensus is that it’s getting worse, not better. What to do? While no panacea, the basics apply — current anti-virus with daily updates, autoupdate on operating systems, good Internet hygiene — don’t open unknown mail, don’t download unknown things, keep a watchful eye for phishing attacks, use good passwords and don’t share them. I think this will be our best/only approach for some time to come.
When I used to fly in the service, one of the safety concerns was ‘complacency’. Complacency was letting down your guard because of a feeling of safety based on numerous previous flights where nothing bad had happened. System X never failed, system Y hadn’t failed, system Z had failed a little bit, but there was a backup, etc. Per a recent McAfee and Office Depot survey, small to medium sized businesses (SMB’s) are suffering from a similar thing.
From a study of over 1000 participants, a majority (66%) felt confident that their devices and data were safe from hackers. Further, 77% felt they had never been hacked. This feeling of security is inconsistent with the evidence of SMB’s increasingly being targets of cyber attacks. According to a statement by Congressman Chris Collins, part of the reason for this complacency is that attacks on small and medium sized businesses typically don’t make the news. However there are a lot of them, hence the long tail. According to McAfee, another reason for the increasing malicious activity on SMB’s is that larger businesses have had some success in hardening their enterprises to cyberattack and that has shifted the effort-invested and payoff balance for cyber criminals.
The study also found that 45% of the SMB’s responding did not secure data on employee’s personal devices and 14% hadn’t implemented any security measures at all.
 A significant vulnerability has been found in the latest version (WNDR3700v4) of Netgear’s N600 Wireless Dual-Band Gigabit Router. Per the researcher with Tactical Network Solutions that discovered the flaw, it is “trivially exploitable” and allows the attacker to disable authentication, open up a backdoor (telnet session), and then return the router to its original state so that the user never knows it was open. According to PC World, other routers may be affected as well.
A significant vulnerability has been found in the latest version (WNDR3700v4) of Netgear’s N600 Wireless Dual-Band Gigabit Router. Per the researcher with Tactical Network Solutions that discovered the flaw, it is “trivially exploitable” and allows the attacker to disable authentication, open up a backdoor (telnet session), and then return the router to its original state so that the user never knows it was open. According to PC World, other routers may be affected as well.
To mitigate the risk:
The Register reports that a vulnerability has been discovered in several home and small business router models made by D-Link. The vulnerability allows unauthenticated users to gain administrative access to the router’s Web interface, thereby providing access to the network behind the router. Per the post, models include DIR-100, DI-524, DI-524UP, DI-604S, DI-604UP, DI-604+ and TM-G5240 units.
Because there is no current fix, users should disable admin access via wireless connection.
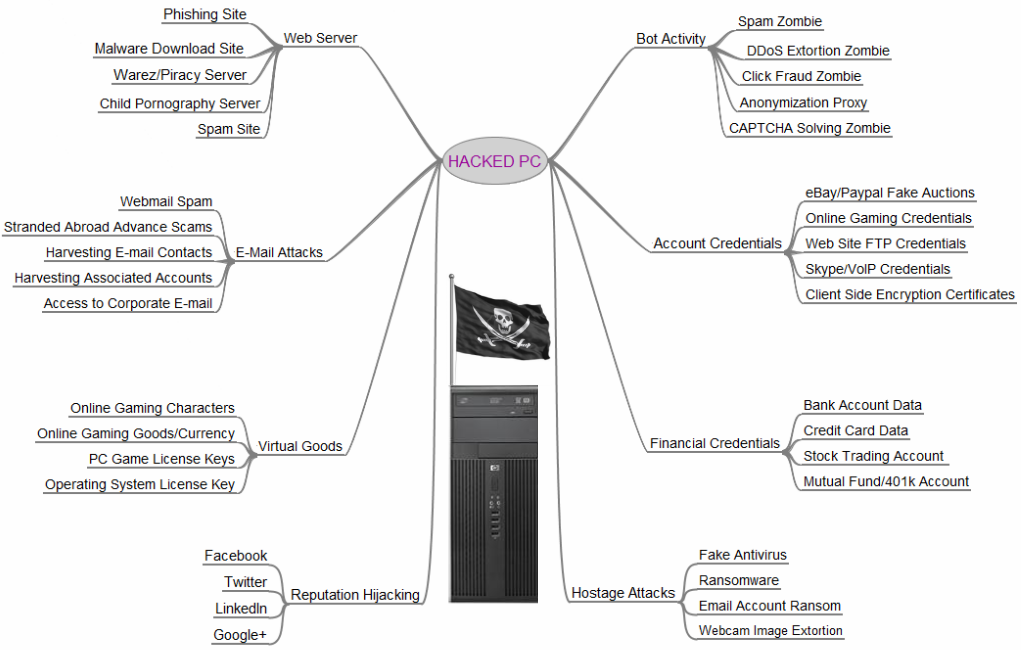
via krebsonsecurity.com
 The Federal government is seeking to motivate businesses that operate our nation’s critical infrastructure systems to voluntarily adopt a Cybersecurity Framework currently under development by NIST (National Institute of Standards and Technology). These systems include the electricity generation and distribution grid, transportation systems, and drinking water storage and distribution systems. A preliminary draft is available now here and it will also be presented in two weeks at the University of Texas.
The Federal government is seeking to motivate businesses that operate our nation’s critical infrastructure systems to voluntarily adopt a Cybersecurity Framework currently under development by NIST (National Institute of Standards and Technology). These systems include the electricity generation and distribution grid, transportation systems, and drinking water storage and distribution systems. A preliminary draft is available now here and it will also be presented in two weeks at the University of Texas.
Roughly simultaneously, the Departments of Homeland Security, Treasury, and Commerce have been developing various options to try to provide incentives for companies to voluntarily adopt the Framework. Per the White House Blog, there are eight core areas or approaches to incentives under consideration.
While these are proposals for incentives for critical infrastructure companies, I’m wondering if some of these can serve as a model for SMB’s for adoption of cybersecurity standards for SMBs. Adjusting cyber insurance premiums based on participation would seem to be an obvious approach. However, as has been discussed previously, a mature cyber insurance market does not yet exist and it’s not a slam dunk that one will evolve sufficiently fast to address this need. For SMB’s seeking government grants, to include SBIR (Small Business Innovation Research) grants, compliance with an SMB cybersecurity framework would seem to be a no brainer. Also, optional public recognition for compliance with an SMB cybersecurity framework would seem to be a practical approach.
What would motivate you as an SMB to adopt an established Framework?