The just-released 2013 ENISA (European Union Agency for Network and Information Security) Threat Landscape report is consistent with Mick Jagger’s prescient 1978 prediction of the state of cybersecurity, captured here:
Don’t you know the crime rate
Is going up, up, up, up, up
To live in this town you must be
Tough, tough, tough, tough, tough
A number of known threats continue, attack tools are increasingly sophisticated, more nation-states are becoming proficient with these tools, and the mobile ecosystem is a ripe new battlefield. On the upside, reporting and information sharing between organizations has increased and vendor turn around in response to new vulnerabilities is faster.
I can’t give it away on 7th avenue — cheap and plentiful devices

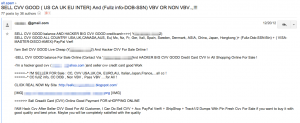
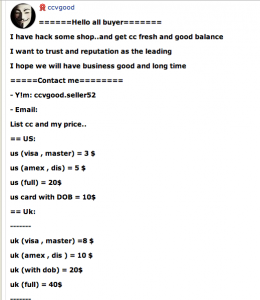
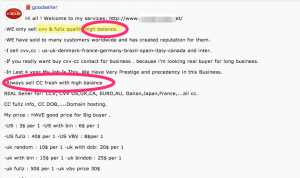
While known to be a factor for some time, a newcomer to the threat list is the Internet of Things (IoT). IoT are networked devices that move, control, sense, surveil, video/audio, and otherwise collect and share information from and with the environment. Development tools and production for these networked devices and systems are cheap and billions more are expected in the next couple of years. (There’s even a conference preparing a road map for a trillion sensors in the next several years.)
Low security is the rule rather than exception for these devices and large amounts of data are being generated. The ENISA report says, “smart environments are considered the ultimate target for cyber criminals.” For example, preliminary work for phishing attacks can be augmented by gaining information about where a victim’s smart home is, picking up information leakage from their integrated media devices (Xbox One is doing more than just playing Halo), accessing what a user’s energy usage profile might be, etc. ENISA calls out the following top emerging threats in the Internet of Things space:
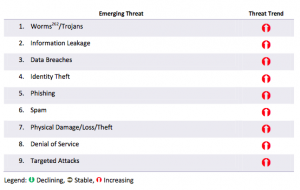 Other threats identified include:
Other threats identified include:
- Differences in many different smart appliances lead to large variances in context and content of transmitted data, opening avenues for cybercriminals.
- Devices built on embedded systems, some of which have not yet been widely deployed. Some of these embedded cores (of many different types and manufacturers) will have unknown and unpublished functions and many will be difficult to maintain (keep patched). Look at the recent D-Link saga.
- Many devices built on embedded systems do not communicate operational status to the user, eg “I am working,” “I am actively collecting data on your environment, “I am behaving erratically,” “I am off,” etc.
- Increased data creation leads to increased data storage amounts, data concentration, and corresponding increased bandwidth requirements/loads. Even a little bit of analysis can result in a significant increase in resources. Remember the basic database join (or even simpler Cartesian product) ? — you start with three elements in one list (A,B,C), but want to relate them to data in another list (D,E,F), so you relate them in a third table and you have (AD,AE,AF,BD,BE,BF,CD,CE,CF). If each element used say 1 MB of space, your initial storage and bandwidth requirement quadrupled from 6 MB (A + B + C + D + E + F) to 24 MB (A + B + C + D + E + F + AD + AE + AF + BD + BE + BF + CD + CE + CF).
For me, the other thing about Internet of Things (IoT) devices is that we often don’t really think of them as sensing, computing, analyzing, data collecting and transmitting devices. Many seem innocuous and, often, we don’t even know they’re there.
Life’s just a cocktail party
Finally, assuming that these IoT devices have already been vetted by somebody else (like the store that we bought it from) is, unfortunately, flawed logic. Businesses large and small will be rushing to market with typically insecure devices and they won’t be taking the time to analyze all of the use cases of how their product could be misused. As consumers, we need to develop the skill of thinking, ‘how could this device be misused? ‘ Most of us aren’t used to thinking like that. A family in Texas learned that the hard way a few months ago with their baby monitor. In general, if a device operates over the network and we can see it, then somebody else can see it.
Shadoobie.
[chart images from http://www.enisa.europa.eu/activities/risk-management/evolving-threat-environment/enisa-threat-landscape-2013-overview-of-current-and-emerging-cyber-threats]
 A team of researchers has identified a way to extract full 4096-bit RSA decryption keys just by listening to (detecting) the sounds generated by a computer. Sound patterns can be associated with particular processes occurring on the computer. Of special interest are the unique sound patterns generated when cyphertext (text that has been encrypted) is in the process of being decrypted. The researchers claim that in less than an hour a decryption key can be identified by analyzing sound patterns generated by decryption of particular cyphertexts. Interestingly, this is not sound generated by fans, hard drives, or speakers, but rather sound generated by electronic components such as inductors and capacitors.
A team of researchers has identified a way to extract full 4096-bit RSA decryption keys just by listening to (detecting) the sounds generated by a computer. Sound patterns can be associated with particular processes occurring on the computer. Of special interest are the unique sound patterns generated when cyphertext (text that has been encrypted) is in the process of being decrypted. The researchers claim that in less than an hour a decryption key can be identified by analyzing sound patterns generated by decryption of particular cyphertexts. Interestingly, this is not sound generated by fans, hard drives, or speakers, but rather sound generated by electronic components such as inductors and capacitors.